A relatively new ransomware, ProLock, has paired up with the QakBot banking trojan to access victims’ networks. ProLock’s leveraging of QakBot gives it bolstered persistence, anti-detection and credential-dumping techniques.
ProLock ransomware first emerged in March as a successor to another recent malware strain, PwndLocker, and has made its mark targeting financial, healthcare, government and retail organizations. ProLock’s first big attack targeted major ATM provider Diebold Nixdorf at the end of April.
“ProLock uses many similar techniques as other ransomware operators to achieve their goals,” said Oleg Skulkin, senior digital forensics analyst at Group-IB in a recent analysis. “At the same time, however, the group does have its own unique approach. With more and more cybercrime groups showing interest in enterprise ransomware deployment campaigns, some operators may be involved in deploying different ransomware families, so we’ll likely see more overlaps in tactics, techniques and procedures.”
ProLock relies uses unprotected Remote Desktop Protocol (RDP) servers with weak credentials to infect some victims, a fairly common technique for ransomware operators (including Nefilim, Nemty, Crysis and SamSam). However, researchers said the “more interesting” infection vector is QakBot.
QakBot
QakBot is a trojan, affiliated with the MegaCortex ransomware and known to be loaded via the Emotet malware in previous campaigns. QakBot is typically distributed via phishing emails with attachments of weaponized Microsoft Office documents (or links to malicious documents that are located on cloud storage). A victim first must download the weaponized document via the email, and then enable macros. Then, PowerShell is launched and used to download and run the QakBot payload from the command-and-control (C2) server.
The use of QakBot by ProLock plays into an existing cybercrime trend. More malware strains have been forming partnerships to help them fill in each other’s skill-set gaps. For instance, the operators behind TrickBot and IcedID started a collaboration in 2018, while Ryuk has used TrickBot and Emotet malware in its attack chain.
 QakBot brings a slew of new capabilities that elevates ProLock’s ransomware attack vector: It not only has keylogging capabilities, but is also able to run additional scripts like Invoke-Mimikatz (a PowerShell version of Mimikatz) – allowing the attacker to employ credential dumping by pulling multiple passwords from the machine. Using this technique, ProLock operators can sniff out privileged credentials and then use these to start network discovery activities, such as port scanning and Active Directory reconnaissance.
QakBot brings a slew of new capabilities that elevates ProLock’s ransomware attack vector: It not only has keylogging capabilities, but is also able to run additional scripts like Invoke-Mimikatz (a PowerShell version of Mimikatz) – allowing the attacker to employ credential dumping by pulling multiple passwords from the machine. Using this technique, ProLock operators can sniff out privileged credentials and then use these to start network discovery activities, such as port scanning and Active Directory reconnaissance.
“In addition to a wide variety of scripts, attackers use AdFind – another popular tool used by many ransomware groups – to query Active Directory,” said researchers.
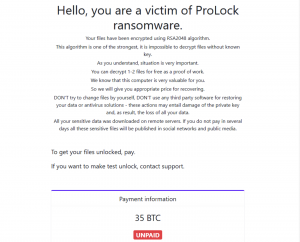
ProLock then uses RDP to move laterally across networks and collect data, which it then exfiltrates using a command-line tool (Rclone) that’s capable of synching files to and from different cloud storage providers, such as OneDrive and Google Drive. At the same time, the ransomware encrypts the files (adding a .proLock, .pr0Lock or .proL0ck extension to each encrypted file) and leaves a note for the vitim asking them to make a payment in order to unlock their files (the sample researchers analyzed asked for a 35 Bitcoin payment, or $312,000). According to BleepingComputer, the ransomware operators typically demand six-figure ransom payments in exchange for unlocking data.
Other Features
The use of RDP and QakBot for initial infection gives ProLock operators an upper hand in terms of persistence and detection evasion. For instance, the operators use valid accounts for RDP access to gain persistence in the network. The ProLock payload is also hidden inside a bitmap image file (BMP) or JPG file, which researchers said may be considered a defense evasion technique as well.
And, “QBot has a neat trick that lets it avoid detection: it checks for the newest version of itself, and replaces the current version with the new one,” researchers said. “Executable files are signed with a stolen or fake signature. The initial payload, downloaded by PowerShell, is stored on the server with a PNG extension. What’s more, is that it’s replaced with the legitimate file calc.exe after execution.”
While many ransomware families (like Maze and Sodoniki) are turning to technique called “double extortion,” where they threaten to publish the data stolen in addition to asking for a ransom to unlock the data, ProLock don’t appear to be relying on this tactic yet.
“Unlike their peers, though, ProLock operators still don’t have a website where they publish exfiltrated data from companies that refuse to pay the ransom,” said researchers.
Concerned about the IoT security challenges businesses face as more connected devices run our enterprises, drive our manufacturing lines, track and deliver healthcare to patients, and more? On June 3 at 2 p.m. ET, join renowned security technologist Bruce Schneier, Armis CISO Curtis Simpson and Threatpost for a FREE webinar, Taming the Unmanaged and IoT Device Tsunami. Get exclusive insights on how to manage this new and growing attack surface. Please register here for this sponsored webinar.











