It was a short hiatus for the REvil ransomware group that signed off in July following several high-profile attacks by the Russia-based crew on such companies as global meat processor JBS and tech services provider Kaseya.
The cybercrime gang shut down its dark web sites, including its public and payment sites and a negotiation portal – in mid-July as pressure mounted following the Kaseya attack, including from U.S. lawmakers and the Biden Administration, which promised stronger responses to ransomware attacks and put pressure on Russian President Vladimir Putin stop such campaigns emanating from the country.
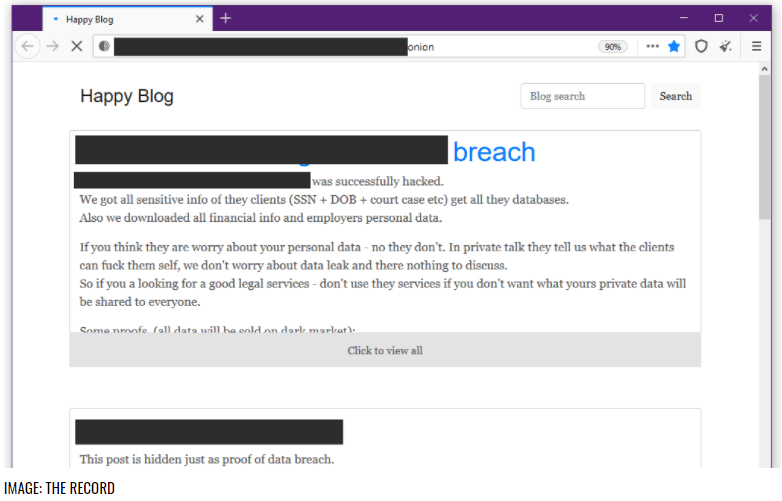
However, security researchers this week said REvil’s Happy Blog – a website that REvil operators used to list those victims who refused to negotiate or pay a ransom – had reappeared, indicating a return by the group.
At the same time, the gang’s payment portal, where victims were sent to negotiate with the cybercriminals, has also been restored at the same dark web .onion URL, according to a blog post by cybersecurity firm Recorded Future.
Renewed REvil Activity
Some cybersecurity firms are seeing renewed activity by the REvil group.
“REvil is back, and not just their leak sites,” AJ King, CISO at incident response expert BreachQuest, told eSecurity Planet. “New variants of Sodinokibi [another name for REvil] ransomware have started to show up on VirusTotal with compile dates of 9/4, and we should expect new waves of ransomware infections to show up in the coming months.”
Ivan Righi, cyber threat intelligence analyst with digital risk protection firm Digital Shadows, also said there has been new activity around REvil. Happy Blog became active on Sept. 7, and “a new victim was posted on the website on September 8, 2021, but the group has not yet announced why their site previously disappeared for months. This new victim was also posted on Dopple Leaks, the data leak site for the DoppelPaymer ransomware, on March 1, 2021.”
News of the revival of the REvil spread quickly this week. Brett Callow, threat analyst at antivirus vendor Emsisoft, posted a tweet about the situation, writing, “Unfortunately, the Happy Blog is back online.”
Significant Ransomware Threat
Before shutting down in July, the notorious ransomware-as-a-service (RaaS) group had been an active player and a driver in the escalation of ransomware attacks and ransom demands. The attack on JBS in late May – which was linked to REvil by the FBI – targeted corporate servers in North America and Australia. It was later learned that JBS paid an $11 million ransom to quickly get its systems back up and running. It was half of what the REvil bad actors had initially demanded.
A month later it was revealed that Kaseya also had been hit by a REvil ransomware attack just days before the July 4 weekend. The group reportedly said it had shut down millions of servers and demanded a $70 million ransom. However, less than two weeks later the group shut down its websites, Kaseya officials said the company had obtained a universal decryptor key from a third party and that it was sharing with affected customers.
The company didn’t reveal where the key came from, but some have speculated it was a gesture of conciliation from Russia to U.S. law enforcement officials.
Further reading: How DMARC Can Protect Against Ransomware
U.S. Reaction to Attacks
The National Security Council after the JBS attack sent a memo to U.S. companies urging them to take the threat of ransomware and other attacks seriously and the White House said President Biden’s administration was raising the issue with Russian officials. In addition, a spokesperson said Biden spoke to Putin about the ongoing ransomware problem during a meeting.
The attacks were part of a string connected to REvil and also part of a sharp increase in ransomware attacks worldwide during the first half of 2021. According to a report by Atlas VPN, the number of ransomware attacks in the first six months of the year spiked 151 percent year-over-year, hitting 304.7 million attacks. Another report from Fortinet found that ransomware activity was 10 times more than a year ago.
Ransomware Groups Fill the Void
REvil shut down its operations two months after DarkSide – another notorious ransomware group that was behind the attack that shut down Colonial Pipeline and resulted in fuel shortages in the United States, particularly in the Southeast – did the same. The closing down of both operations led to a surge in attacks by cybercriminal gangs that moved in to fill the resulting void. It included the resurgence of the LockBit RaaS, which was used in a high-profile attack on global consulting firm Accenture in which these bad actors sought about $50 million, as well as attacks by LockFile and Ragnar Locker.
The return of the REvil sites was unwelcome news, but not totally unexpected, according to some experts. Cybercriminal groups are known to shut down during the summer for extended periods of time, BreachQuest’s King said, adding that public scrutiny around its operations likely had little influence on the REvil gang’s decision in July.
“Criminal organizations that effectively operate with impunity and make billions of dollars are not going to shut down permanently due to some bad press,” he said. “If anything, they will reform under another name and begin operations again as normal. I would fully expect for DarkSide to come back and begin ransomware operations. It is far too profitable for them to just walk away.”
Cybercrime Pays
Oliver Tavakoli, CTO at cybersecurity firm Vectra, also wasn’t surprised at REvil’s return, noting the lucrative nature of ransomware and the “relationships of convenience” among people involved.
“Whether they congregate under an existing brand or invent a new one comes down to their sense of a brand’s equity,” Tavakoli told eSecurity Planet. “Does it make more sense to create a new brand or bring an existing one out of hiatus? REvil has sufficient brand equity that it has come back. I expect the same to be true for Darkside – unless REvil and others end up taking their business share away in the meantime.”
Digital Shadows’ Righi said there are many reasons why REvil dropped out of sight in July, from the pressure put on by law enforcement after the Kaseya attack to the desire to simply take a break. That said, he called the group’s return “fairly surprising.”
“Ransomware groups do not typically return after shutting down operations – and when they do, they typically reemerge as a rebranded ransomware,” he said. “The motivation for the return could be a variety of reasons.”
Being out of the spotlight for a couple of months may have lifted some of the law enforcement pressure, or there might have been disagreements within the gang whether to continue operations, which has been seen in other groups like Babuk Locker, he said.
“It seems unlikely that DarkSide would make a return, as the group has been inactive since May 2021, and affiliates have likely moved to other ransomware groups,” Righi said.
Further reading: How Zero Trust Security Can Protect Against Ransomware






